Unraveling the Veil: Understanding RTLO & LTRO Hacking Techniques
In the realm of cybersecurity, deception knows no bounds. RTLO and LTRO hacking techniques have emerged as crafty means to manipulate text direction, leaving users vulnerable to sophisticated attacks. This article dives into the cryptic world of Unicode-based tricks, shedding light on how to thwart these threats and safeguard our digital journeys. Get ready to decode the secrets of text manipulation and fortify your defenses against cyber adversaries!
Understanding RTLO and LTRO Attacks
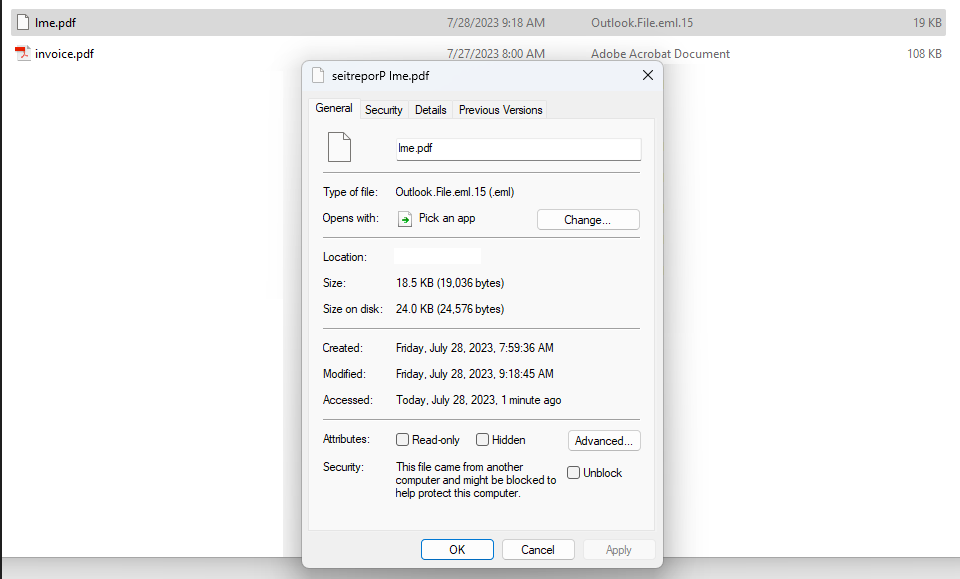
LTRO and RTLO attacks are phishing techniques used by cybercriminals to trick people into clicking on malicious links or opening harmful files. These attacks take advantage of the way computers handle certain special characters in text.
- Left to Right Override (LTRO) Imagine you are reading a book in English, which goes from left to right. In an LTRO attack, the cybercriminal sneaks a hidden character into a web link or file name that tells the computer to start reading the text from left to right again. This hidden character resets the normal reading direction, making it seem like the link or file name is safe and familiar. For example, a link that looks like “google.com” might have an LTRO hidden character, so when you click on it, you end up on a fake website designed to steal your information.
- Right to Left Override (RTLO) On the other hand, imagine reading a book in a language that goes from right to left, like Arabic or Hebrew. In an RTLO attack, the cybercriminal adds a sneaky character that reverses the text direction, making it appear different from what it actually is. For instance, a link that appears to be “amazon.com” may have an RTLO hidden character before “amazon,” so when you click on it, you’re taken to a malicious website instead of the real Amazon site.
Here’s a simple example of how an RTLO attack can be used:
Legitimate Text: “example.com”
Text with RTLO Attack: “moc.elpmaxecom”
In the second example, the “Right-to-Left Override” character is used to reverse the text after “example” and make it appear as “moc.elpmaxe,” leading the user to potentially click on a malicious link.
In both attacks, the cybercriminals try to deceive you by making the links or file names look legitimate at first glance, but they’re actually leading you to dangerous websites or files that could harm your computer or steal your personal information.
How do RTLO and LTRO attacks operate?
First let me explain, the term of “Unicode”. Unicode is like a special system that gives every letter, symbol, and language in the world a unique number. This way, computers can understand and work with text from any language or writing system, like English, Chinese, Arabic, and many more.
In Unicode, each character gets its own special code, which is like a secret number. For example, the letter “A” has the code U+0041, and “B” has the code U+0042. These codes are written in a special way using numbers and letters.
Unicode covers not only regular letters but also lots of cool stuff like emojis, math symbols, and hidden control characters. So, it’s not just for languages but for all sorts of text-based elements.
This system is super important for modern technology. It lets software developers create apps and websites that can handle text from different languages smoothly. No matter where you are in the world or what device you’re using, Unicode ensures that the information you see and share stays accurate and consistent. It’s like a universal translator for computers!
However, some people can misuse it for something called an “RTLO attack.”
In an RTLO attack, a specific Unicode character, U+202E, is used to play tricks with the way text is shown. Normally, this character is used for legitimate reasons, like handling mixed text with different writing directions, like English mixed with Arabic. But malicious actors use this character in a sneaky way. When they insert it into a text, it makes the text that comes after it appear in the opposite direction.
These tricks can lead to confusion, especially in things like phishing emails, where scammers try to trick you into clicking on dangerous links. They make the link look safe in one direction but lead to a harmful website in the opposite direction.
How can we safeguard ourselves against RTLO and LTRO?
Protecting ourselves against RTLO and LTRO attacks requires a proactive approach. Here are some essential steps to follow:
- Source Verification: Prioritize file source verification. Exercise caution when dealing with files from unknown origins, particularly those received via emails or instant messages. Always validate the sender’s identity and ensure the authenticity of the file before opening it.
- Email Safety Measures: Safeguard your email by enabling spam filters and utilizing email security features. By doing so, you can significantly reduce the likelihood of receiving malicious emails. Avoid engaging with links or attachments from unfamiliar or untrusted sources.
- Antivirus Software: Maintain the security of your system by keeping your antivirus and security software up to date. Consistently scan your system for potential threats, ensuring you detect and eliminate any emerging risks promptly.
- Manual File Execution: Adjust your system settings to prompt for confirmation before executing or opening files. This extra layer of caution enables you to assess the legitimacy of a file before it is allowed to run.
- URL Verification: Exercise vigilance when clicking on links. Before clicking, hover your cursor over the link to preview the destination URL. Verify that it aligns with the message’s context and appears authentic.
- Data Backup: Establish a regular routine for backing up your important files and data. Maintain backups on external storage devices or cloud services. This proactive approach ensures that, in the event of a malware attack, you can restore your data without resorting to paying ransoms.
In conclusion, safeguarding our digital lives against RTLO and LTRO attacks necessitates a proactive and vigilant approach. By adhering to the fundamental steps outlined in this article, we can significantly fortify our defenses and reduce the risk of falling victim to malicious tactics.
Sources: Krebs on Security. (2023, August 4). Teach a man to phish and he’s set for life. Retrieved from https://krebsonsecurity.com/2023/08/teach-a-man-to-phish-and-hes-set-for-life/
Cybriant. (2023, August 5). What is a Right-to-Left Override Attack? Retrieved from https://cybriant.com/what-is-a-right-to-left-override-attack/

Nice article Margaux! Well explained. I did not know about RTL/LTR Override attacks yet.