The Cybersecurity Dilemma

The Security Dilemma
The cybersecurity dilemma was developed from another concept, the security dilemma.
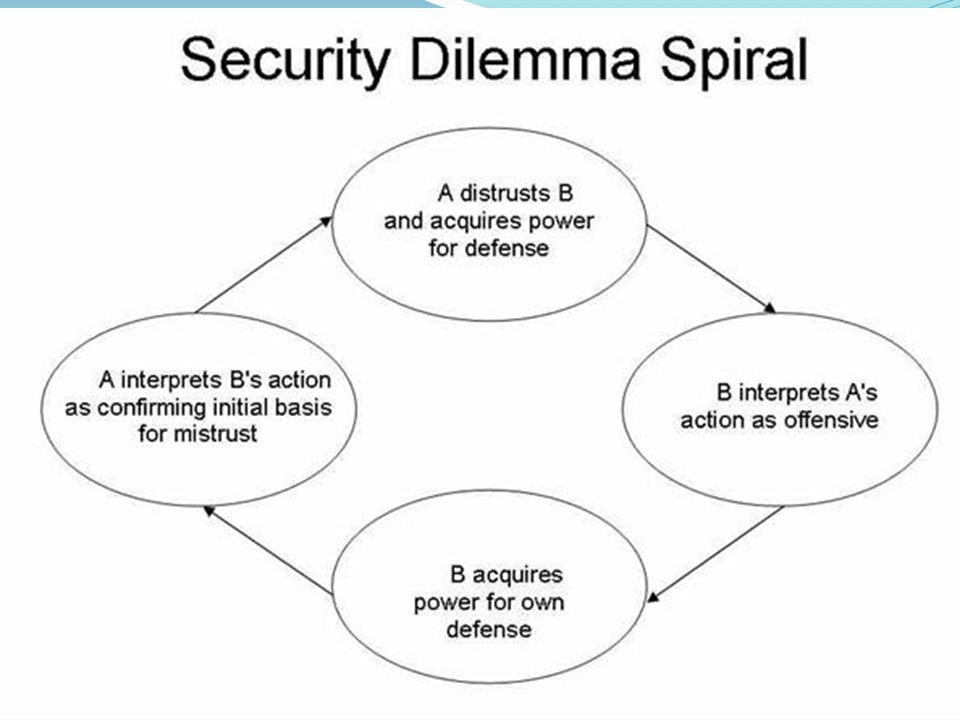
In political science, a security dilemma is a scenario in which measures taken by a state to increase its own security provoke responses from other states, resulting in a decrease rather than an increase in the original state’s security. According to some foreign relations experts, the most critical cause of disagreement between states is the security dilemma. They argue that in the international scene, there is no world government and that, as a result, each state is responsible for its own stability. As a result, states’ primary aim is to optimize their own defense.
However, many of the steps taken to achieve that aim, such as arms acquisition and the implementation of advanced military capabilities, would inevitably reduce the security of other nations. Decreased defence of other states would not immediately produce a dilemma, but other states will tend to follow suit if one state arms. They have no way of knowing if the arming state will use its enhanced military capability to launch an offensive in the future. As a result, they will either opt to strengthen their own military forces in order to restore the balance of power, or they will conduct a preemptive strike to deter the arming state from disrupting the balance in the first place.
The Cybersecurity Dilemma
Much like the security dilemma, the cybersecurity dilemma is created when states, in order to ensure their own cybersecurity, intrude into the strategically critical networks of other states, threatening, unintentionally, their protection, causing escalation and weakening stability.
States will obtain vision into their potential adversaries’ political leadership, and conduct counterintelligence by penetrating each other’s networks. In other words, infiltrating an adversary’s computer systems will result in significant benefits for a state. Even a state that only wishes to build offensive options has a clear motivation to initiate intrusions ahead of time because on the other hand, a network attack can lead to significant damages. To mitigate this danger, states expend a lot of money and effort attempting to deter and track intrusions into their critical infrastructure. As part of this defense initiative, any states will hack into the networks of other states to collect threat intelligence. As a result, intrusions can be motivated by defence goals.
Unlike the security dilemma, the cyber security dilemma poses more problems. Indeed, most of what instinctively gives defenders advantages in traditional combat, such as the capacity to position stabilizing defensive fortifications at strategic chokepoints, has no apparent equivalents in cybersecurity. Similarly, distinguishing between defensive and offensive network intrusions is difficult, particularly since intrusions that begin as defensive in nature can easily morph to fit offensive goals.
The state is at the forefront of this problem but since it is a multi-state dilemma, answers cannot be sought exclusively by inter-state coordination. Rather, if we want a safe and robust cyberspace, we must aggressively combat a strategically exploitable cyberspace full of vulnerabilities. This is a compromise that certain state actors must make if they want a form of national security that includes cyberspace. If such a solution is not reached, the pursuit of greater national security will still mean less cyber-security, which will always mean less national security due to weaknesses in sensitive infrastructure. This is where states can further strengthen cyber-security by enacting new regulations.
Sources:
- Anders Wivel, ‘Security dilemma’, (2010), https://www.britannica.com/topic/security-dilemma
- Ben Buchanan, ‘The Cybersecurity Dilemma: Hacking, Trust, and Fear Between Nations’, (2017)
- Myriam Dunn Cavelty, ‘Breaking the Cyber-Security Dilemma: Aligning Security Needs and Removing Vulnerabilities’, (April 2014)
