Cyber Threat Intelligence
What is Cyber Threat Intelligence (CTI)?
In recent years, CTI has been a hot issue in Information Security, however the absence of a literature study on defining the idea, as well as the tendency for corporations to adopt their own definition to differentiate their product, may lead to some uncertainty. There are numerous alternative meanings for this concept. As ambiguous as it may be, CTI can be defined broadly as evidence-based knowledge about a current or arising threat, including context, mechanisms, indicators, implications, and actionable advice, that can be used to inform decisions about the subject’s response to that menace or hazard. According to this concept, the organization may decide its action at the strategic, operational, and tactical levels by collecting information that contains specifics about present and emerging threats.
How is CTI created?
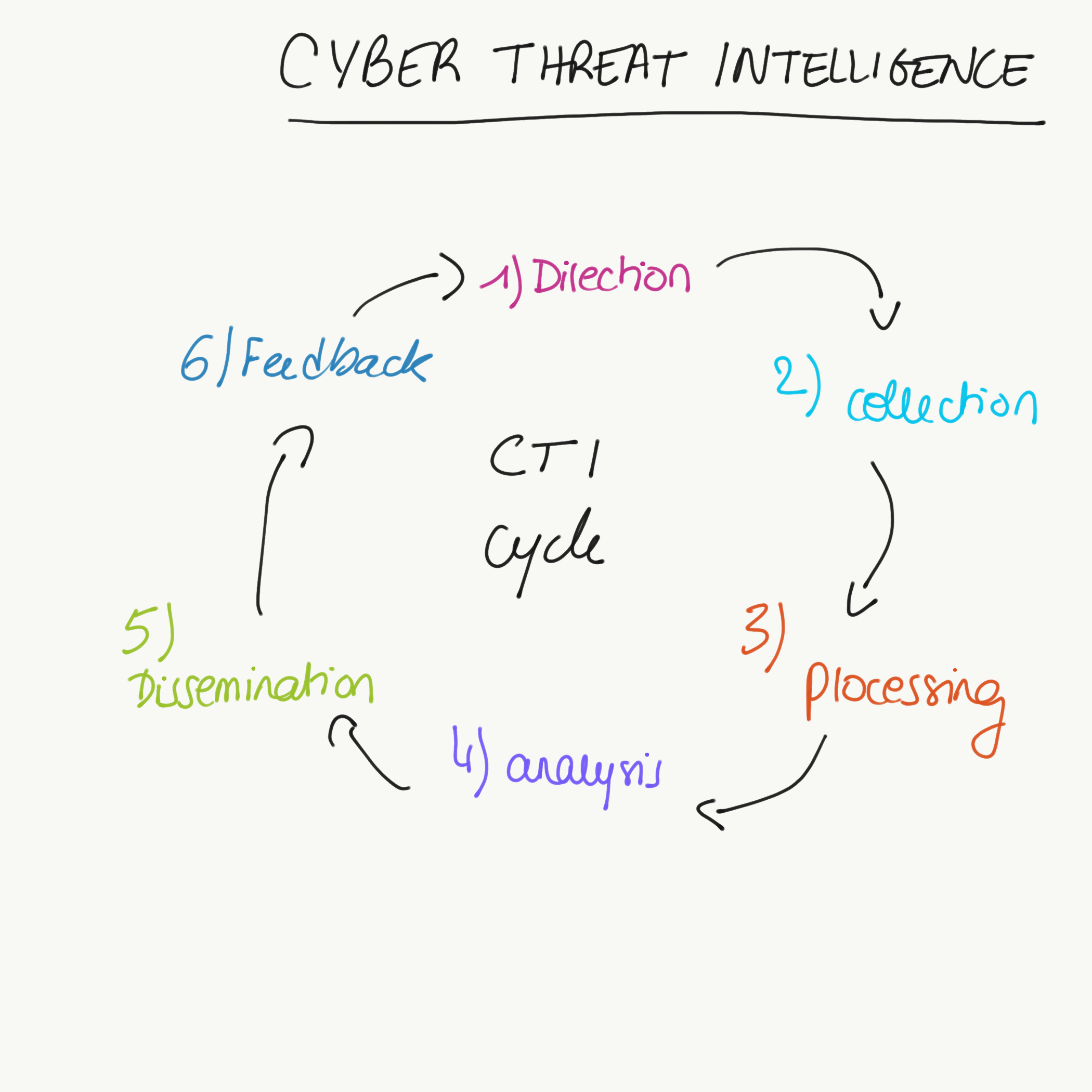
Raw data is not the same as intelligence. CTI is the end product of a six-part data collecting, processing, and analysis cycle.
- Planning and direction
To generate actionable threat intelligence, the first step is to ask the appropriate question. The questions that best promote the generation of actionable threat intelligence are those that focus on a specific fact, event, or activity. Broad, open-ended queries should be avoided.
2. Collection
The following step is to collect raw data that meets the standards established in the first stage. It is important to collect data from a variety of sources, including internal sources such as network event logs and records of previous incident responses, as well as external sources such as the open web, the dark web, and technical sources.
3. Processing
After gathering all of the raw data, it has to be sort, structure with metadata tags and filter out data redundancy or false positives and negatives.
4. Analysis
The next stage is to make sense of the data that has been processed. The purpose of analysis is to identify possible security vulnerabilities and alert the appropriate teams in a way that meets the intelligence criteria stated during the planning and directing stage.
5. Dissemination
After that, the final product is disseminated to its target users. To be actionable, threat intelligence must reach the right people at the right time.
6. Feedback
After getting the completed intelligence product, the person who submitted the initial request evaluates it to see if their queries were answered.
CTI is divided into three subcategories:
- Strategic: relatively broad trends usually intended for a non-technical public
- Tactical: outlines of threat actors’ strategies, approaches, and processes for a more technical audience
- Operational: technical information about various cyberattacks and initiatives
Challenges with CTI
- Fail to make the most of threat intelligence programs due to an excessive volume of threat data and a lack of employee knowledge,
- According to a Ponemon research, 70% of threat intelligence feeds are suspect and untrustworthy in terms of quality,
- When working with CTI, there are privacy and legal considerations to address, including how data may be exchanged and which laws regulate data sharing.
Sources:
Dalziel H. How to Define and Build an Effective Cyber Threat Intelligence Capability. Elsevier Science & Technology Books, 2014; 2014.
Robinson M, Jones K, Janicke H. Cyber warfare: Issues and challenges. Comput Secur. 2015;49:70–94.
Sergei Boeke J van de BDP. Cyber Threat Intelligence – From confusion to clarity; An investigation into Cyber Threat Intelligence. 2017.
