Cyber Attacks in Cloud Computing
Today, I felt like discussing about cloud computing because it seems like everyone is talking about it, and some individuals who aren’t especially interested in computer-related things could find it intriguing to learn more about it because they most certainly use it as well. So, there you have it.
What is Cloud Computing?
Cloud computing is a catch-all word for anything involving the delivery of hosted services through the internet. A cloud may be both private and public. A public cloud offers resources to anybody with access to the internet. A private cloud is a private system or database servers that provides hosted services to a small number of users with restricted access and rights.
The purpose of cloud computing, whether private or public, is to give simple access to computer resources and IT services. Cloud computing means allowing client devices to access data and cloud applications from distant physical servers, databases, and computers over the internet.
These services are classified into three forms of cloud computing:
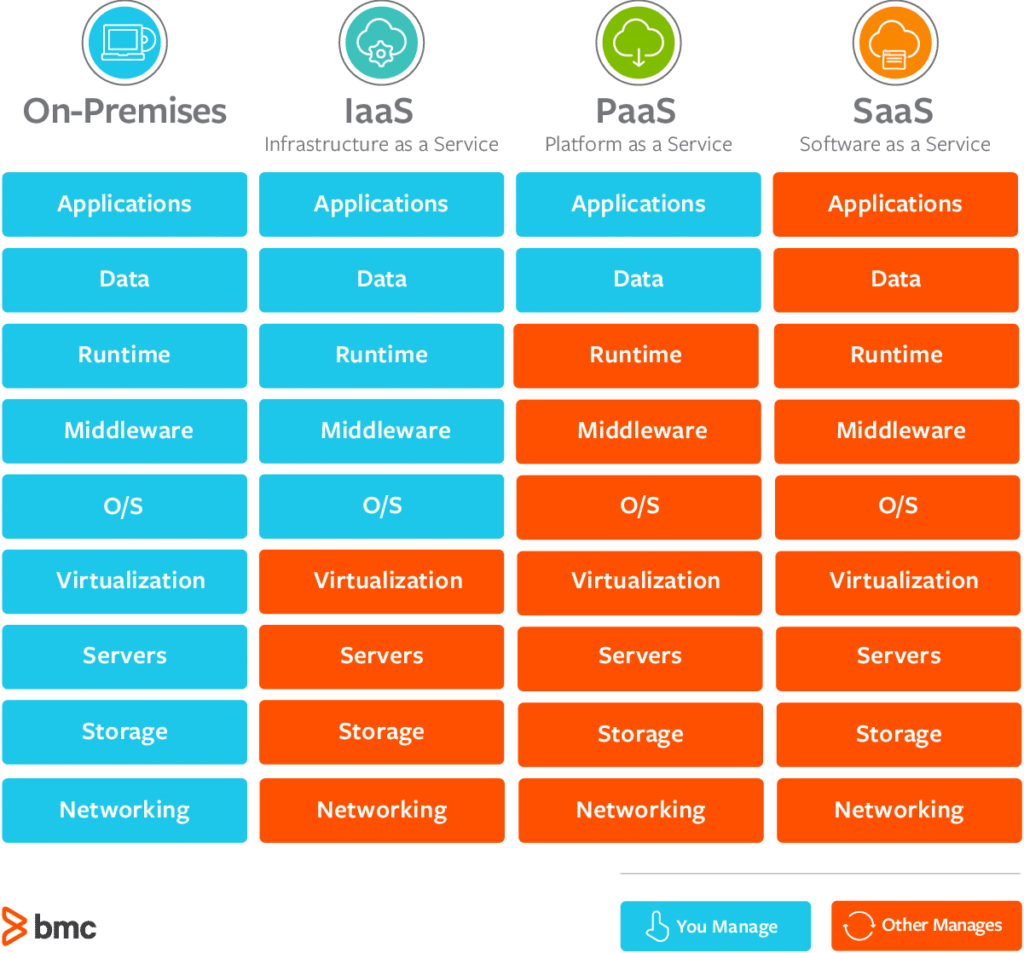
- Infrastructure as a Service (IaaS):
IaaS refers to a cloud service provider managing your infrastructure which means the physical servers, network, virtualization, and data storage, via an internet connection. The user handles things like the operating system, applications, and middleware, whereas the provider manages any hardware, networking, hard drives, data storage, and servers, as well as outages, repairs, and hardware concerns.
- Platform as a Service (PaaS):
PaaS refers to the provision and management of hardware and an application-software platform by a third-party cloud service provider, but the user is responsible for the applications that run on top of the platform and the data on which the apps rely.
- Software as a Service (SaaS):
SaaS is a service that provides its consumers with a software application that is managed by the cloud service provider. SaaS apps are often online applications or mobile apps that consumers may access using a web browser. Program updates, bug patches, and other regular software maintenance are handled on the user’s behalf.
What is a cyber attack in cloud computing?
A cloud cyber attack is any cyber attack that targets off-site service platforms that provide storage, computing, or hosting services via their cloud architecture. Attacks against service platforms that use service delivery models such as SaaS, IaaS, and PaaS are examples of this.
The primary aims of cloud computing cyber attacks are to obtain access to customer data and to block access to cloud services. Both have the potential to inflict substantial harm to cloud users and undermine trust in the security of cloud services.
When planning cloud-based attacks, hackers typically intrude into communications between cloud users and services or applications by leveraging cloud computing flaws, obtaining users’ credentials elsewhere outside the cloud or acting as a hostile insider.
Most common threats
- Data breaches
Unauthorized persons get access to cloud systems and compromise the data contained in them, resulting in data breaches. The mid-2018 Tesla cloud crypto-jacking disclosed important data, resulting in significant data breaches that were costly. This happened because the company failed to encrypt one of its cloud accounts. Human mistake is the leading cause of data breaches.
- Insider threats
Individuals having valid access to an organization’s cloud systems are generally the masterminds. Insider attacks, whether purposeful or malevolent, will do significant damage to cloud systems. As a result, it is critical to notice, examine, and respond to them as soon as feasible.
- Denial-of-service attack (for more info about DoS)
A denial-of-service attack occurs when a hacker floods a system with more online traffic than it can manage at peak capacity. This causes operations to halt completely, with internal users and consumers unable to access the system, rendering the company unable to operate.
- Misconfiguration
Misconfiguration is one of the biggest risks to enterprises’ cloud-based systems. Most business owners have little familiarity with cloud-based infrastructure, which exposes them to a variety of data breaches that can disrupt their operations.
Understanding the most serious dangers to cloud systems and networks is a critical first step toward avoiding and mitigating them.
Sources:
Chai, W. (2021). What is cloud computing? TechTarget. https://searchcloudcomputing.techtarget.com/definition/cloud-computing
Katrenko, A. (2020). Cloud Computing Attacks: A New Vector for Cyber Attacks. Apriorit. https://www.apriorit.com/dev-blog/523-cloud-computing-cyber-attacks
Red Hat. (2018). Types of cloud computing. Red Hat. https://www.redhat.com/en/topics/cloud-computing/public-cloud-vs-private-cloud-and-hybrid-cloud
Triskele Labs. (2021). Cloud cyber attacks: The latest cloud computing security issues. Triskele Labs. https://www.triskelelabs.com/blog/cloud-cyber-attacks-the-latest-cloud-computing-security-issues
Violino, B. (2020). 11 top cloud security threats. CSO. https://www.csoonline.com/article/3043030/top-cloud-security-threats.html
